Common Phishing Emails are a necessary resource for knowing, organizing, and innovative tasks. Whether you're an instructor, moms and dad, or trainee, these ready-to-use resources conserve time and effort. From educational worksheets for math, science, and grammar to imaginative templates like planners, calendars, and coloring web pages, there's something for everybody. With the ease of printable styles, finding out and efficiency can be enhanced in the house or in the class.
Discover a wide range of customizable designs that cater to numerous needs and ages. These templates make discovering interactive and fun while promoting imagination. Download and install, print, and start utilizing them today!
Common Phishing Emails

Common Phishing Emails
These Factor and Multiple Worksheets are perfect for mastering the math topic concerning factors of numbers like Prime Factor Greatest Common Factors Review the prime and composite numbers and learn the concept of factors and multiples with this worksheet pack. Includes a total of 10 ...
Factoring Worksheets K5 Learning
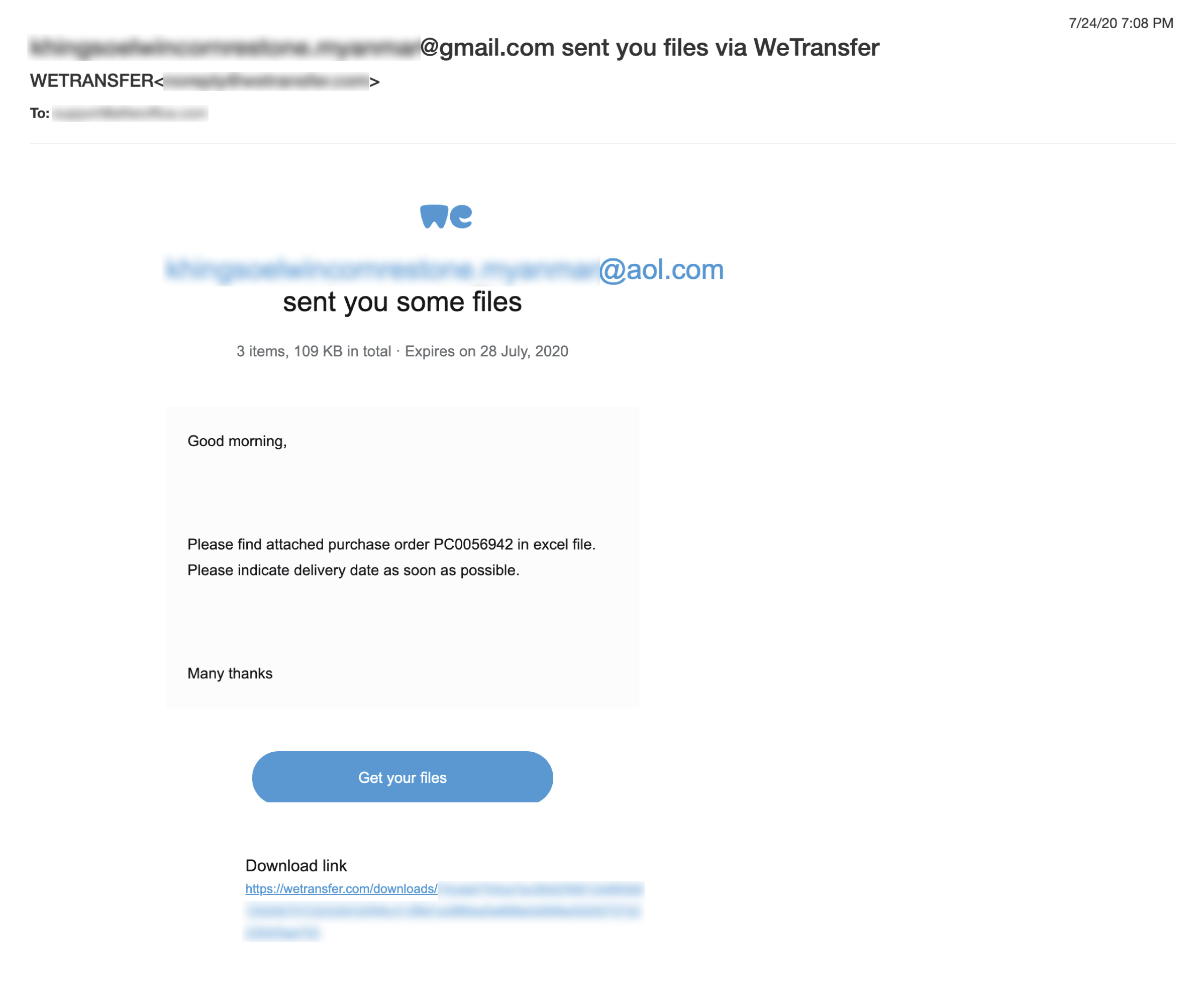
8 Examples Of Common Phishing Emails
Common Phishing EmailsOur factors worksheets feature exercises in factoring numbers, listing out multiples, and drawing factor trees. Practice prime factorization too. Our free factors worksheets provide students with an easy way to practice and master the concept of factoring numbers
Each worksheet is randomly generated and thus unique. You can customize the worksheets by choosing the difficulty level, limits for the numbers to be factored, ... Oltalama Phishing Sald r lar nternetin Karanl k Y z BULB How To Prevent Phishing Attacks 8 Signs Of A Scam Email
Factor pairs worksheet TPT
.png)
Phishing What You Need To Know University IT
A collection of math worksheets on finding factors greatest common factors and factor trees as well as prime numbers composite numbers Complete Guide To Phishing Techniques Mitigations Valimail
List all positive factors of each number 1 8 2 9 3 15 4 16 5 25 6 Best Phishing Email Templates You Know How To Identify Phishing Emails ARDELLES

Report Cox Phishing Email
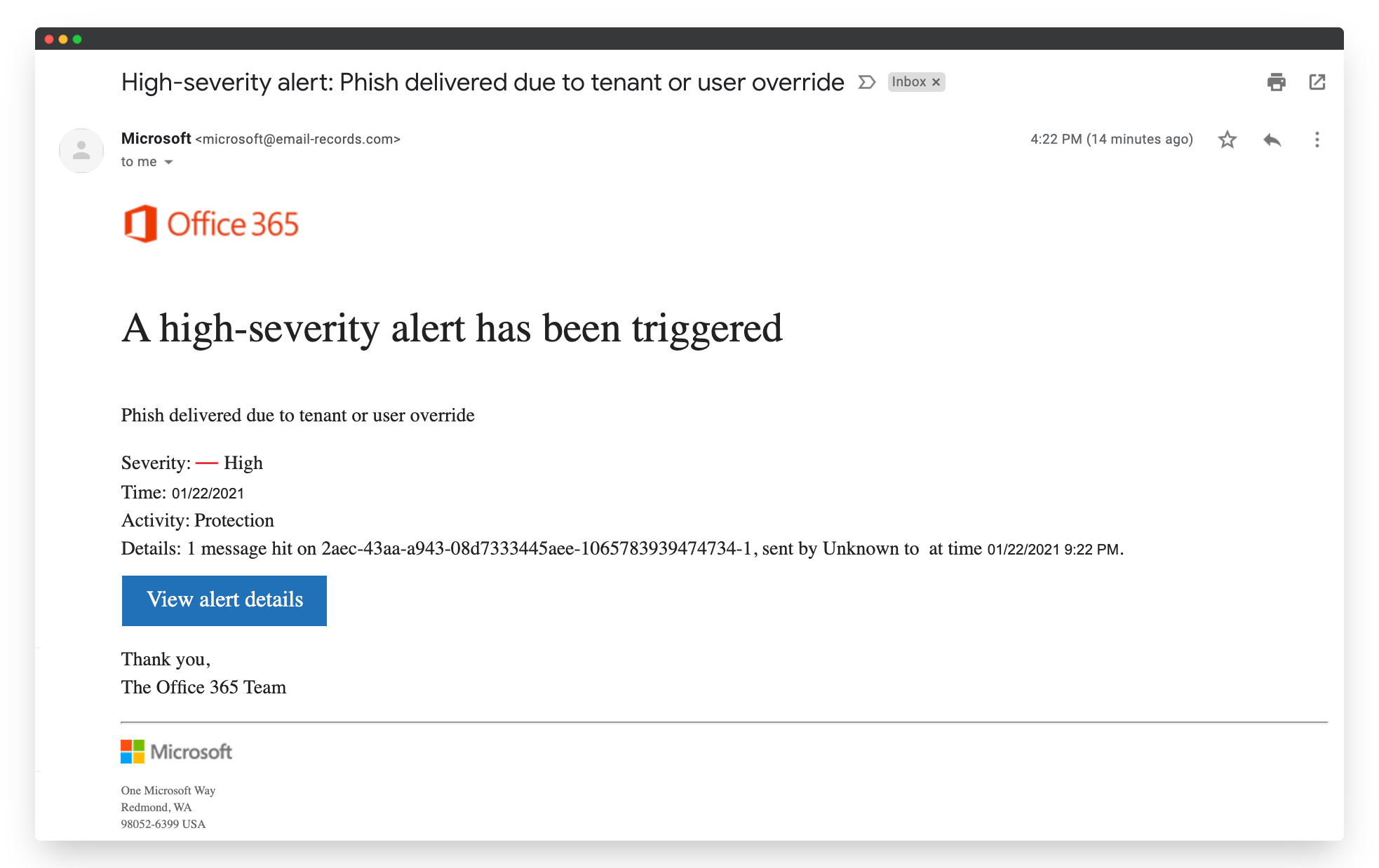
Phishing Scam

Phishing Attacks

Phishing Attacks

Paypal Phishing Examples
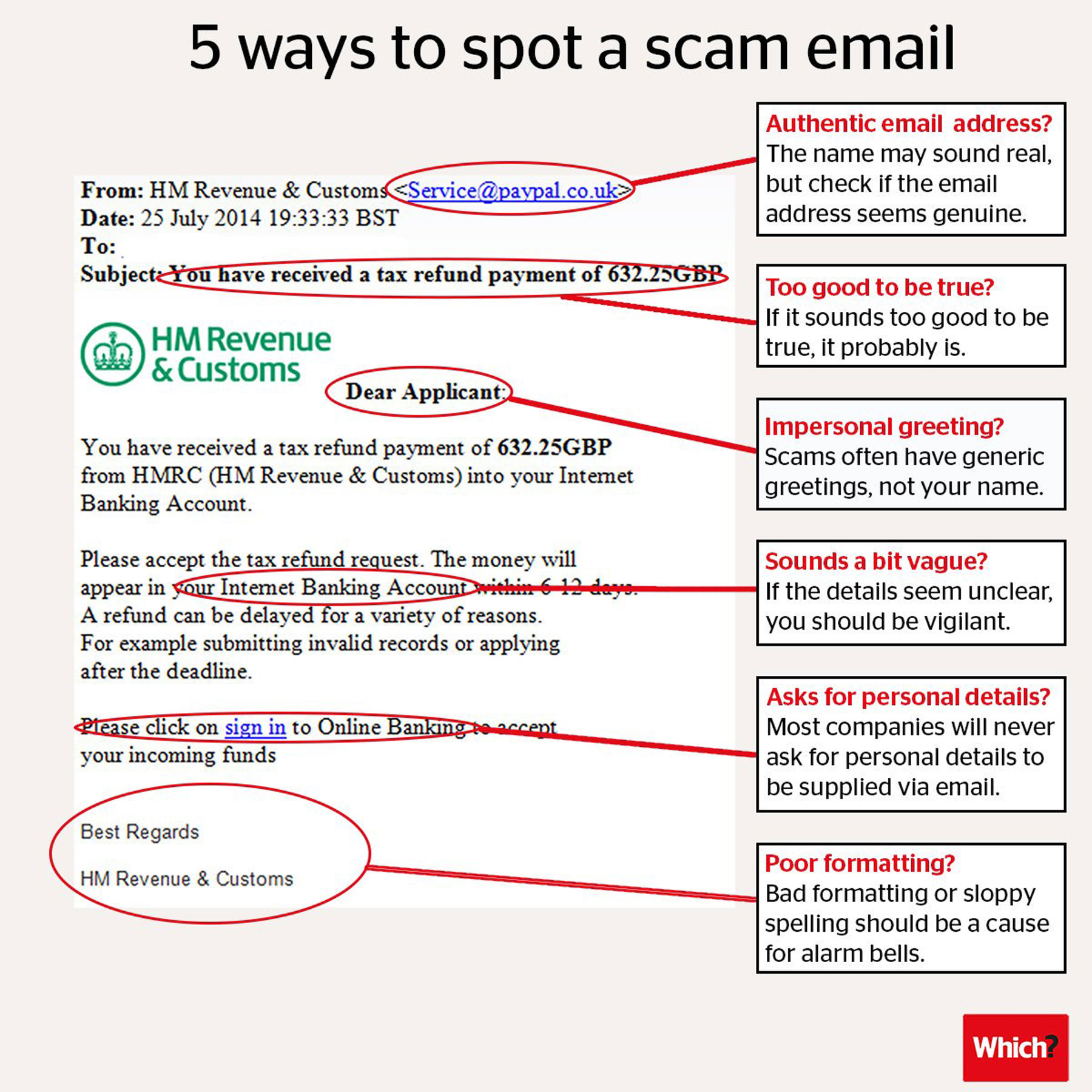
5 Ways To Spot An Email Scam Instantly Frank On Fraud

Phishing Email Example

Complete Guide To Phishing Techniques Mitigations Valimail
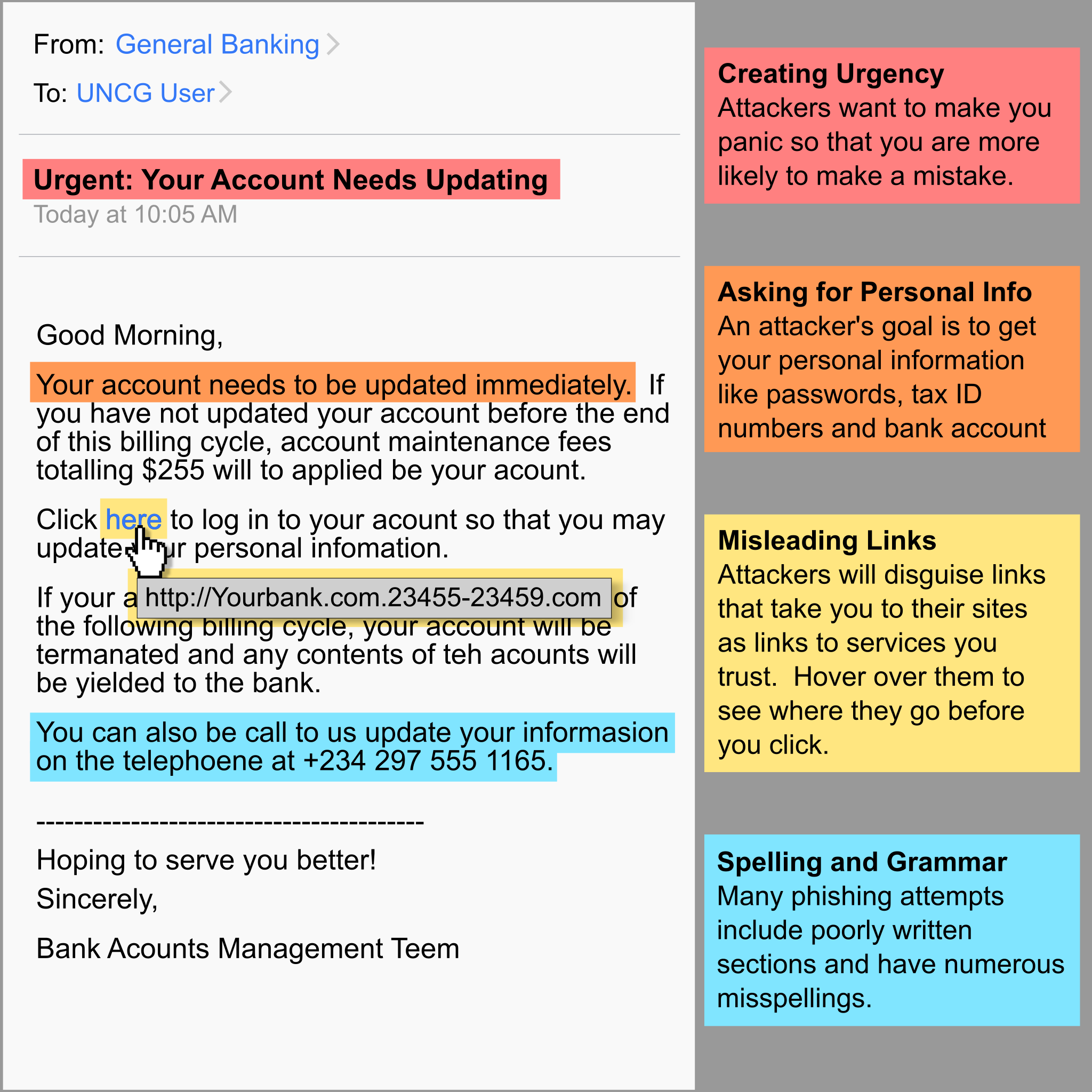
Don t Get Hooked By Phishing Scams Its News Free Nude Porn Photos
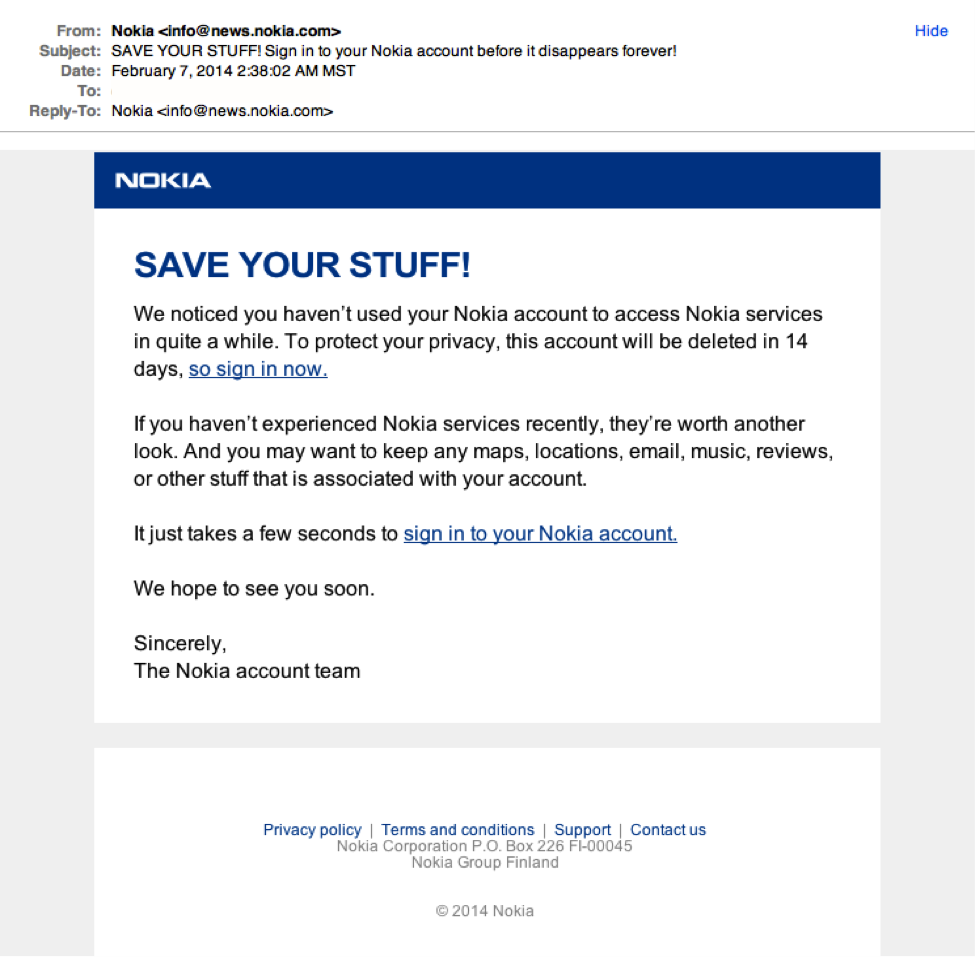
Sample Phishing Email Templates